How to Fix WordPress 429 Too Many Requests Er
WordPress is nowadays officially the most used and popu...

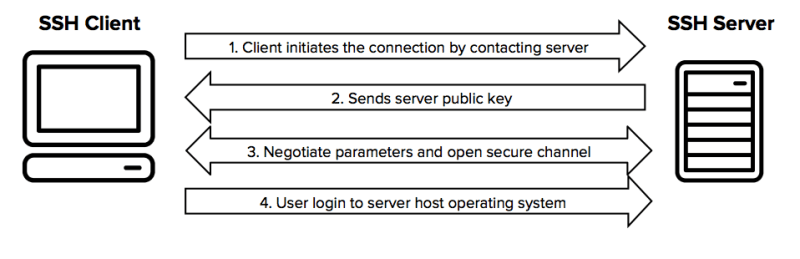
Knowing how to connect to your website via SSH lets you establish certain connections between a local machine and a remote host. These days many businesses are taking advantage of emerging technologies to raise their performance and cut down expenses, and SSH is not separate from this technology.
New signs of progress lead to new requirements, and modern security technology can fight against the useless and weak approaches and methods. This is why we want to dive into the SSH solution.
So keep reading to discover essential tips about SSH, which can make secure and reliable connections for you. Before we cover how to connect your website via SSH, we should know what SSH is.
[lwptoc]SSH stands for secure shell and is a secure communication protocol that initiates the encrypted connections on the network through HTTP(hypertext transfer protocol). HTTP shares data of websites for computers, and SSH adds excellent security to it to access remote resources.
SSH supports different types of server access security, like file transferring and synchronization, FTP over SSH, secure copy, and private network access to the server with OpenSSH. So, you will be able to connect your website using an SSH client to transfer data securely through a GUI or a command line.
Of course, you should at first change the SSH port from its default value to make it truly secure.
Also Read : Port Forwarding on Windows VPS
Tip: As Linux and Mac Os have built-in SSH interfaces, there is no need to install an SSH client.
[rh-cta-wordpress type=”2″]To get started on connecting your site via SSH, you need tools to make it happen. For starters, you should SSH into a server using a terminal that we get to in the following lines so that you will be able to establish a connection through SSH.
[irp posts=”20297″ name=”Telnet vs. SSH| How is SSH different from Telnet in 2022?🔍”]Mac and Linux Os can initiate SSH connections using the Terminal. The Terminal is a kind of emulator similar to DOS, runs commands line instructions both on your system and remote server.
So there is no sign of a graphical user interface to ease making an SSH connection to your host. You have all the essential and valuable options in this simple type-based black screen to come up with the right result.
Putty is a free SSH terminal software known as an SSH client application that runs on Microsoft Windows to access your VPS, physical machine, or multiple virtual machines in one host to manage them. easy to use.
Unlike Terminal, to connect your web server using SSH, you need to download and install Putty first and then head into the next steps.
Putty SSH Client Installation on Windows
Tip: You can choose the package that best fits your Windows version, and it is recommended to download the 32-bit version to be safer.
These two methods do the same thing for you to connect via SSH server from Windows or Mac Os. Once you used SSH client or Terminal as the pre-requirement to connect your host, now let’s go forward with the Command line to run the codes and send commands to the destination server. Now, you should know some information to complete the checklist.
Also Read : Install MikroTik CHR on VPS (Using PuTTY)

After you have successfully connected to your server via the PuTTY SSH client, then you can run the necessary command lines right now.
With these SSH commands, you can move files, delete folders, create new directories, change user permissions, and so on.
ls
cd
mkdir
touch
rm
Note: You need to specify the file name or directory and where you want to copy it. For example: $ cp [options] [source] [destination]
cp
mv
Now let’s see the optional items you can add at the beginning of this command.
clear
tar cvzf ArchiveName.tar.gz /path/to/directory
wget http://fileurl/filename.ext
du
history 50
pwd
find
Also read: Google Chrome Silent Install
Also Read: Generate SSH Keys in Windows 10
Generating Public key authentication for Linux and Mac starts typing commands in the Terminal and using Open SSH.
Tip: You can type a new name or use the default and press enter.
ssh-copy-id -i ~/.ssh/id_rsa.pub user@server
Enter your username instead of the user and server, then the server address you want to use the key authentication.
Tip: You can now authenticate to your server with the key pair.
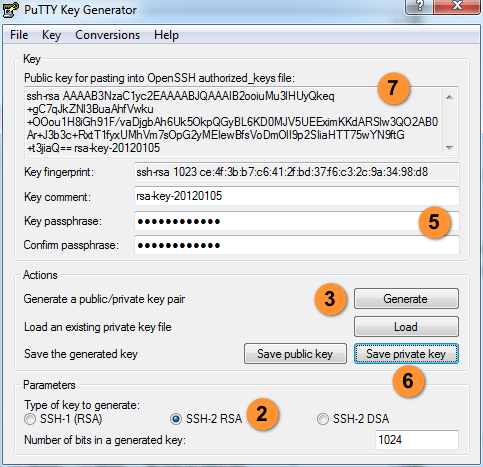
[rh-cta-wordpress type=”2″]Generating a new SSH key is the first thing you need to create the high-security authentication level. It would help if you had this SSH key to connect your server with maximum security for your login process.
When keys are correctly generated, they can guarantee improved security and a fast and convenient way of accessing and managing your servers.
Instead of following up that traditional way using username and password, the Terminal or the SSH client can make it more professional for you.
Also Read: Hosting Multiple Websites on a Single Server
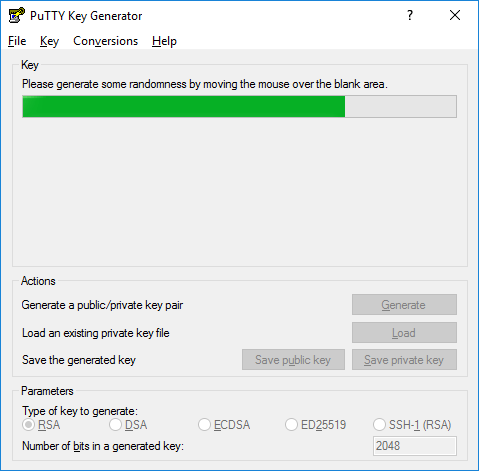
Tip: In this step, start moving your mouse in the window till the green progress bar becomes full.
[irp posts=”6267″ name=”What Is Bootstrap in WordPress? [WordPress Bootstrap Guide for Beginners]The reason is to realize your random movement for the authentication method. This is one of the most reliable techniques you can benefit from the attackers.
Tip: (remember to save the private key it will be needed for the next connection to your machine)
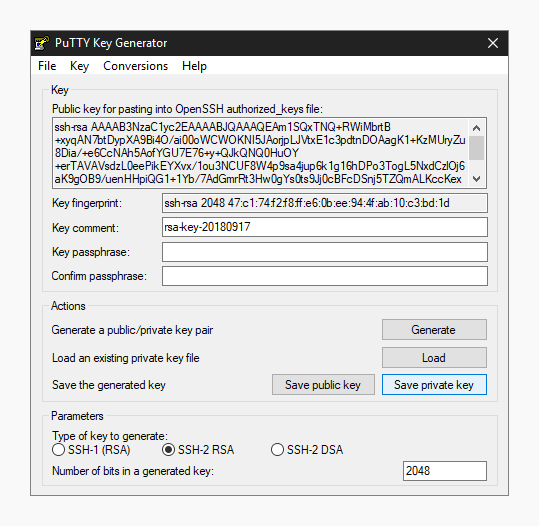
When you have a new key saved on your computer, now you should import it into the PuTTY key agent.
These two steps import the SSH key to the PuTTY
Tip: Enter your key passphrase if it is necessary.
[rh-cta-wordpress type=”2″]Connect to your website via SSH has different advantages and steps that we explain in the context as well as possible. In general, to be a pioneer in this modern world in business communication networks, you need to take a step with high-quality control on your website files and logins on your cloud servers.
Therefore, creating a public key for authentication encrypts your connections to the servers. The private key used by the receiver can decrypt the connection. In the end, this bidirectional process will provide a secure interaction between two network endpoints. Then take it seriously to win, not losing in making interaction in this digital age.
Mary is a creative author who believes content is all about fulfilling users' needs and concerns. She always tries to provide the best solutions for her audience.

WordPress is nowadays officially the most used and popu...

Video content is the most popular type of content by a ...

💡 Note: Looking to set up a secure and efficient VPN...